By Clément Mikula
It’s May 28, 2023, and over 4,000 ETH have been stolen from the Jimbo Protocol.
On Arbitrum, a hacker exploited the rebalancing mechanism of the Jimbo protocol to empty the Trader Joe ETH/JIMBO market pair and escape with the stolen funds to the Ethereum mainnet.
What is the Jimbo Protocol?
The Jimbo Protocol is an experiment on the Arbitrum chain, strongly inspired by the White Lotus protocol and the Olympus DAO.
The goal of this project is to create functional combinations of RFV (risk-free value) and POL (protocol-owned liquidity) and manage them using a Rebalancing mechanism.
Learn more about it here
Theoretically, it could create a token thats price cannot decrease.
How does it work?
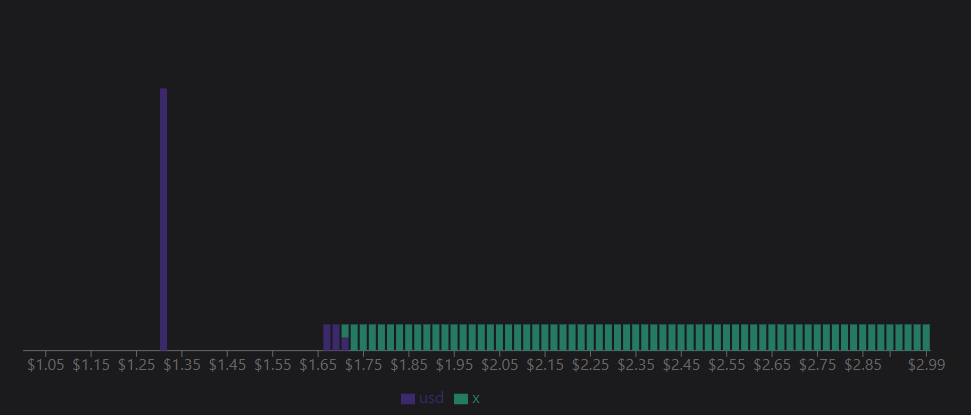
To achieve this, the protocol starts by distributing all the Jimbo tokens in a Trader Joe pool. Trader Joe is a liquidity book DEX, similar to order book markets on TradFi.
Each “bin” represents a price, and contains one of the two tokens in a pair.
eg: a sample of the liquidity distribution in a liquidity book
In this example, the market price can be found at the encounter of the two tokens in one bin, at ~1.70$.
When a user buys x for USD at market price(~1.70 usd), the bin then fills up with usd and sends x to the user, increasing the market price of x since the next user will buy it at the next bin priced at ~1.75 usd.
Once we understand this, we can also understand how Jimbo is able to rebalance itself in order to always support the growth of its tokens.
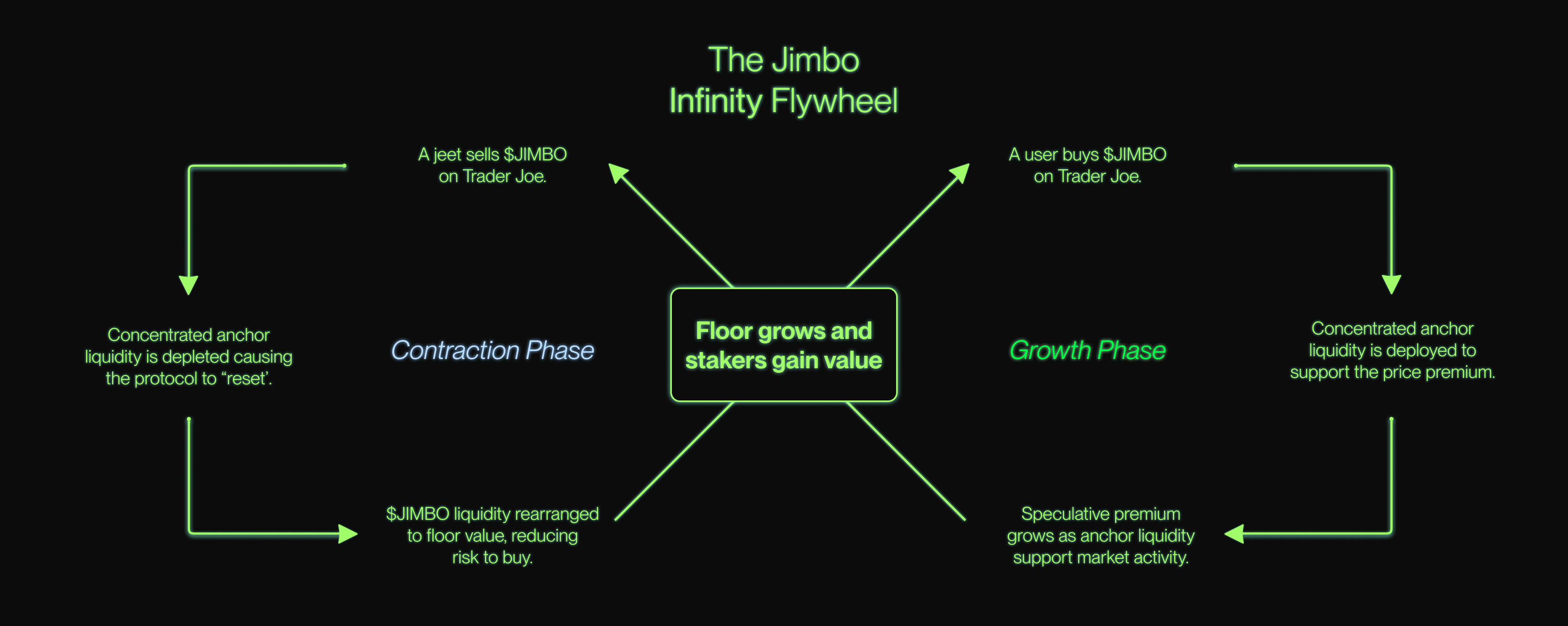
Expansion and Contraction of the Jimbo Protocol
The Jimbo protocol works by using two important bins:
- The floor bin: represents the lowest price to sell Jimbo allowed by the protocol
- The max bin: represents the highest price to buy Jimbo allowed by the protocol
In between these two are all the other bins, allowing for price fluctuations.
The Jimbo protocol expands and contracts its liquidity to support price discovery and absorbs demand using the following two functions:
Shift(): Redistributes 10% of the ETH protocol liquidity around market price and 90% to floor price.
eg:market condition:demand for JIMBO increases, price increases, 5 bins of JIMBO around market price are replaced with ETH.shift()redeploys 10% of the ETH protocol liquidity around the new market price to absorb JIMBO offer.shift()redeploys 90% of the ETH protocol liquidity on the new floor price (calculated using the quantity of ETH in the protocol and JIMBO in circulation)
shiftcreates a liquid market at market price and a solid wall of liquidity if demand for JIMBO declines.Reset(): Redistributes 50% of the JIMBO protocol liquidity around floor bin and 50% in the max bin.
eg:market condition:demand for JIMBO decreases, price decreases, until all ETH bins around market price are replaced with JIMBO.reset()redeploys 1% of the JIMBO protocol liquidity to each of the first 50 bins after the floor bin (50% JIMBO liquidity in total)reset()redeploys 50% of the JIMBO protocol at max bin
resetcreates a liquid market between the market price and the floor price, and another in the max bin, when demand for JIMBO is low.
For a more in depth explanation click here
Contraction and expansion of the liquidity make up the bases of this rebalancing token:
How did the hacker do this?
- Buy JIMBO
- Provide liquidity at a high price (higher than the maxBin)
- Take a flash loan of ~10k ETH
- Buy all JIMBO from the protocol
- Use
shift()to redeploy 10% of the ETH liquidity in the protocol around the market price, now that they are the only provider of JIMBO in the pool - Sell JIMBO for ETH at a manipulated high price (the one they have chosen to provide).
- Move JIMBO liquidity to protocol maxBin (normal price limit)
- Use
reset()to redeploy the Jimbo liquidity in the protocol - repeat step 4 until no more profit is made or until the pool is empty.
- repay the 10k flash loan
After completing this process, the attacker walked away to Ethereum mainnet with most of the ETH/JIMBO pool ETH, about ~4000 ETH valued at ~7,500,000 USD at the time.
How did the Jimbo team react?
Once the news of the exploit spread, the team quickly recognized it and announced the steps they would be taking to recover the funds.
Shortly afterwards they made the hacker an offer, promising to end the legal proceedings and investigation in exchange for returning 90% of the funds.
on Twitter and on-chain (more on this at the end…).
Faced with the attacker’s silence, they finally decided to take legal action with the help of the Department of Homeland Security in New York, which specializes in investigating blockchain-related cybercrime.
What can we learn from this?
Rebalancing tokens is, in theory, an interesting concept to achieve a more “stable” price,
However, a permissionless reordering of the liquidity book can pose a major threat, especially if the rebalancing is based on third-party liquidity providers.
In order to prevent this issue, the protocol could be updated to only redistribute liquidity in protocol range, or to increase the initial supply or the number of bins to make it financially unfeasible for one participant to take total control of the pool.
This issue was addressed in an article about Uniswap v3’s TWAP oracles prices manipulations cost; a TWAP can’t be used in this case but an estimate of the funds needed to take control of the pool can be a very useful metric!
Extra: Find the ultimatum on-chain
Find a transaction from the address of the Jimbo protocol deployer here—
It’s effectively the same one used to deploy the Jimbo contract on arbitrum.
- click on
Click to show more - click on the
View Input Asand chooseUTF-8
Then read the on-chain message the Jimbo team sent to the hacker!
Don’t hesitate to use it to view any messages sent on-chain!